About
Nettarsier is a Startup Company established in 2020.
References

NetTarsier Promotional Video
NetTarsier
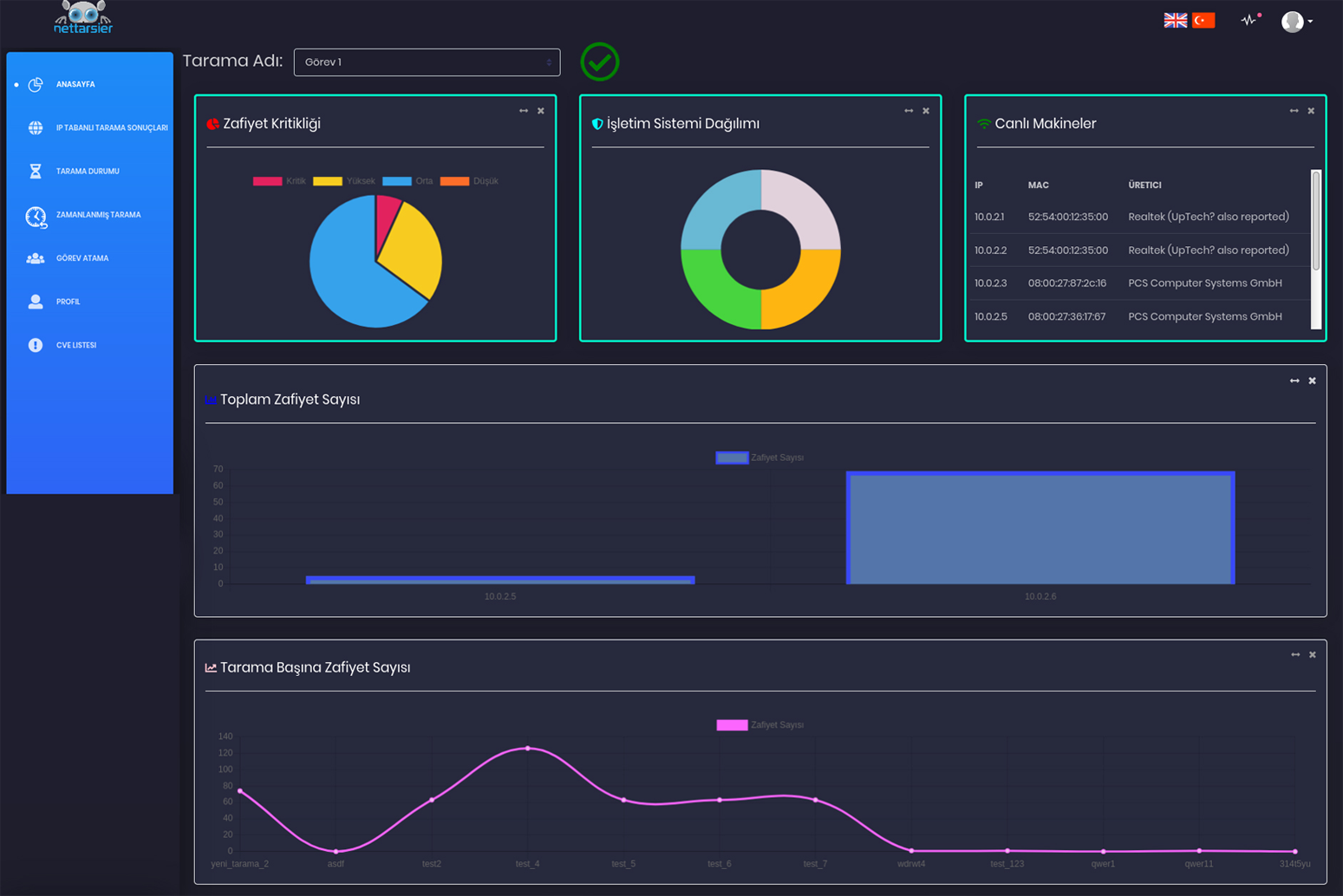
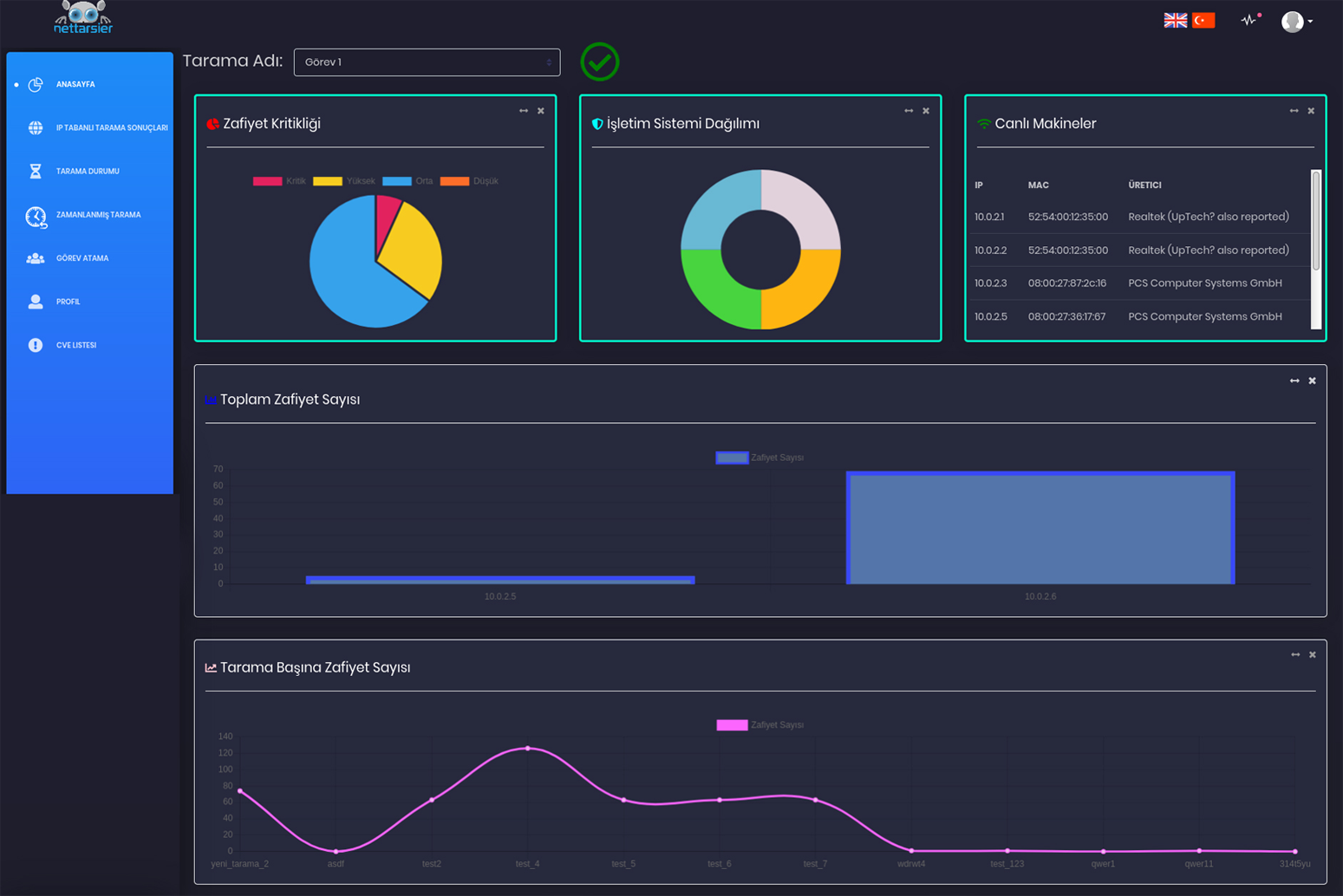
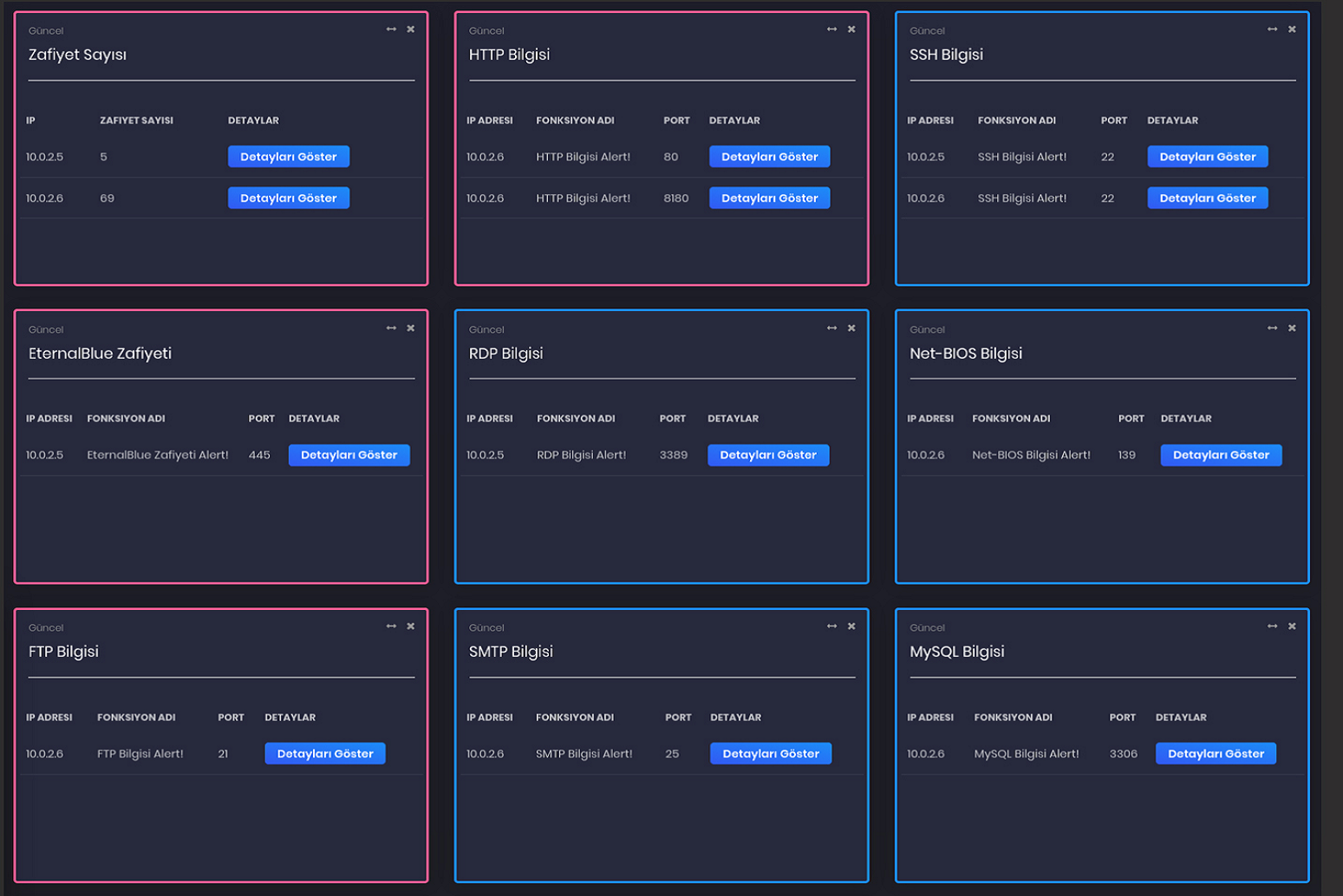
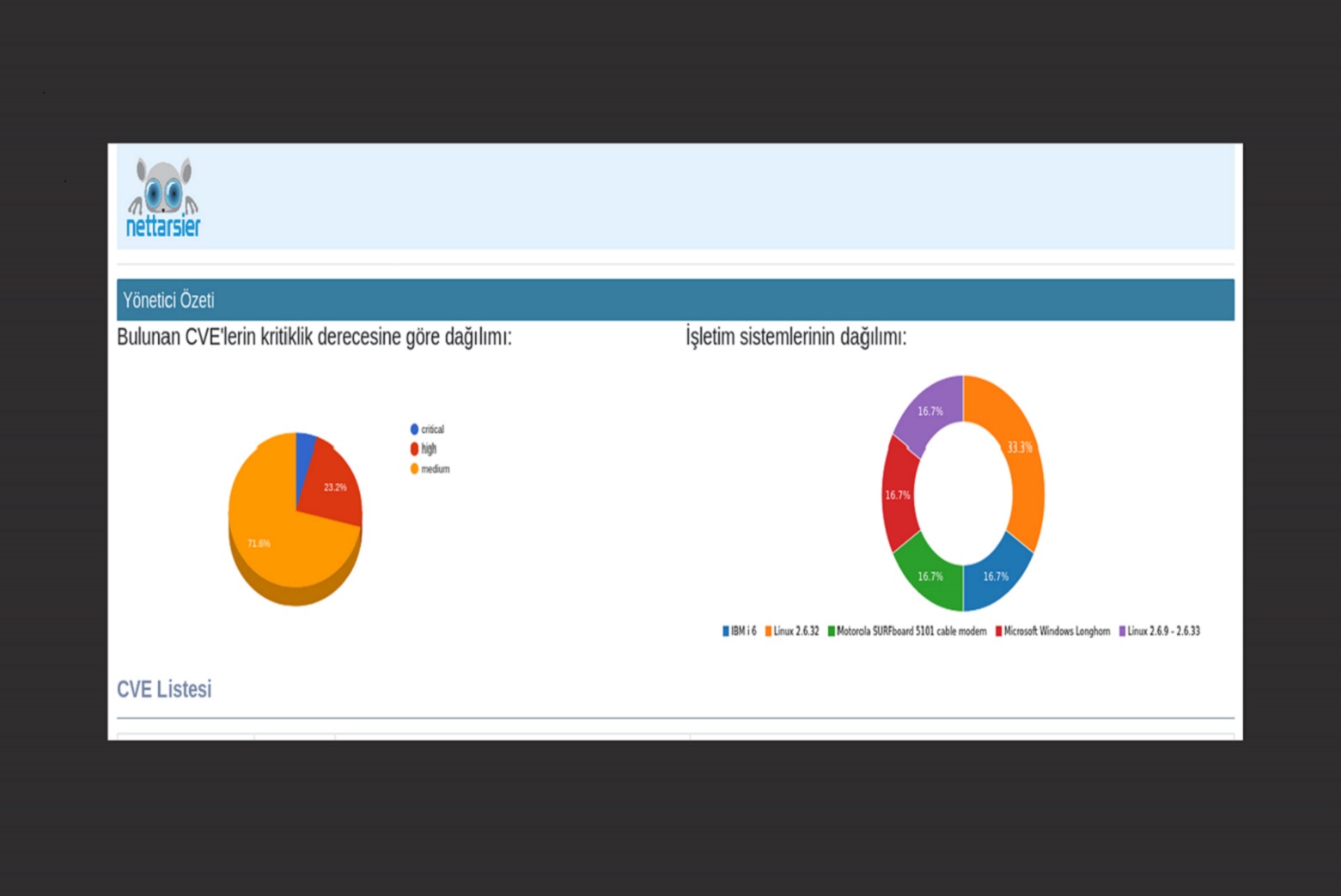
NetTarsier, automatically scans the network and services of the organization in the desired periods, shows the detected vulnerabilities separately on a service-based basis and offers solutions for them, makes it possible to assign task to the vulnerabilities by the department manager, presents all the findings as a result report with the executive summary. It is an extremely fast Enterprise Vulnerability Scanning Tool that can be integrated with other cyber security solutions, including SIEM.
AUTOMATIC SCANNING
It scans the target network and systems periodically and automatically in specified time periods.

HIGH SPEED
With its unique architecture, it completes scanning much faster than alternative vulnerability scanning tools.
SEPARATE OPTIONS PRESENTATION
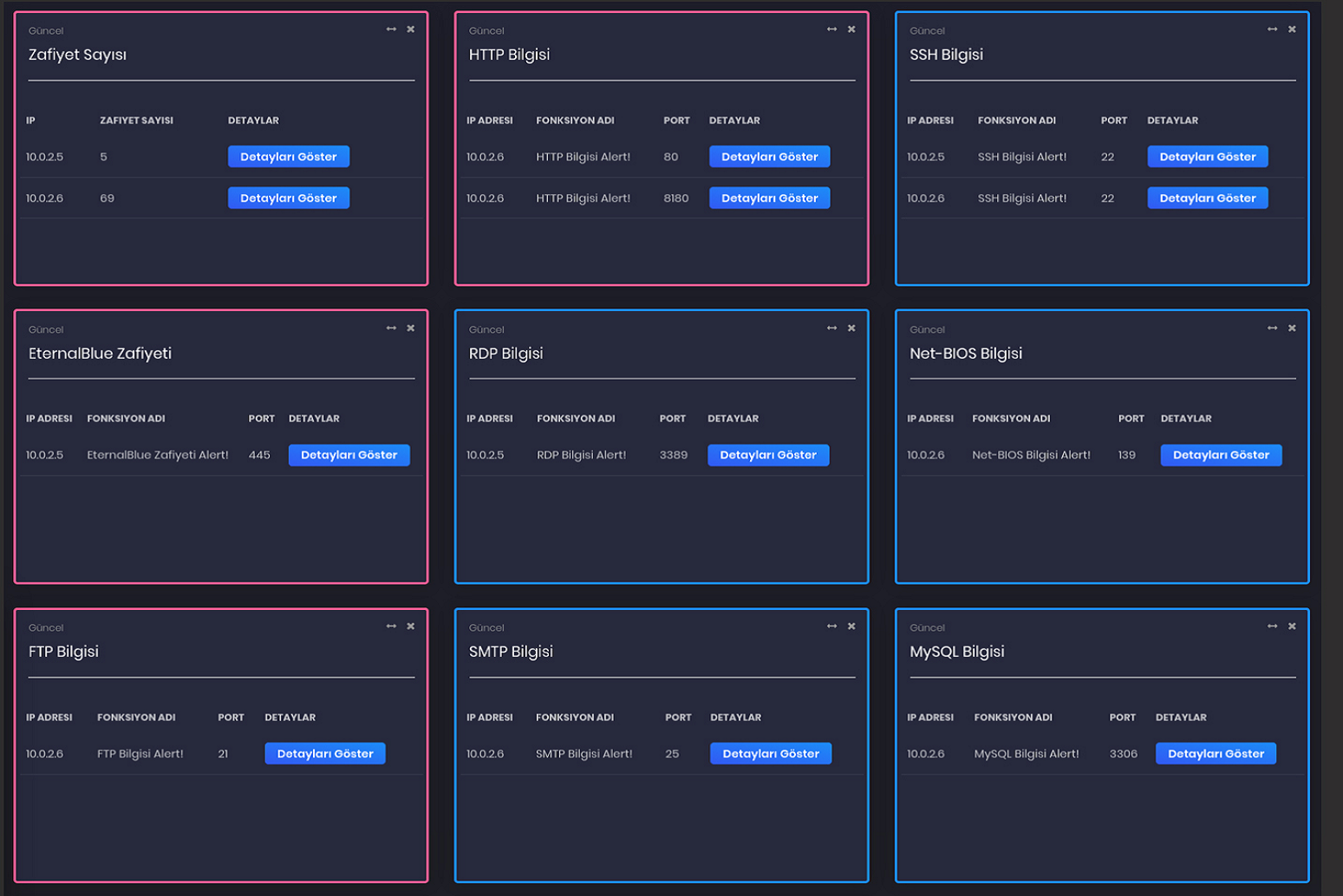
It presents all the critical findings on the main panel screen on a service-based basis.

DETAILED ANALYSIS
It also shows in detail the vulnerabilities detected in that machine for the IP selected at the end of the scan.
SOLUTION PROPOSALS
It offers clear solutions for the most common vulnerabilities detected.

RESULT REPORT
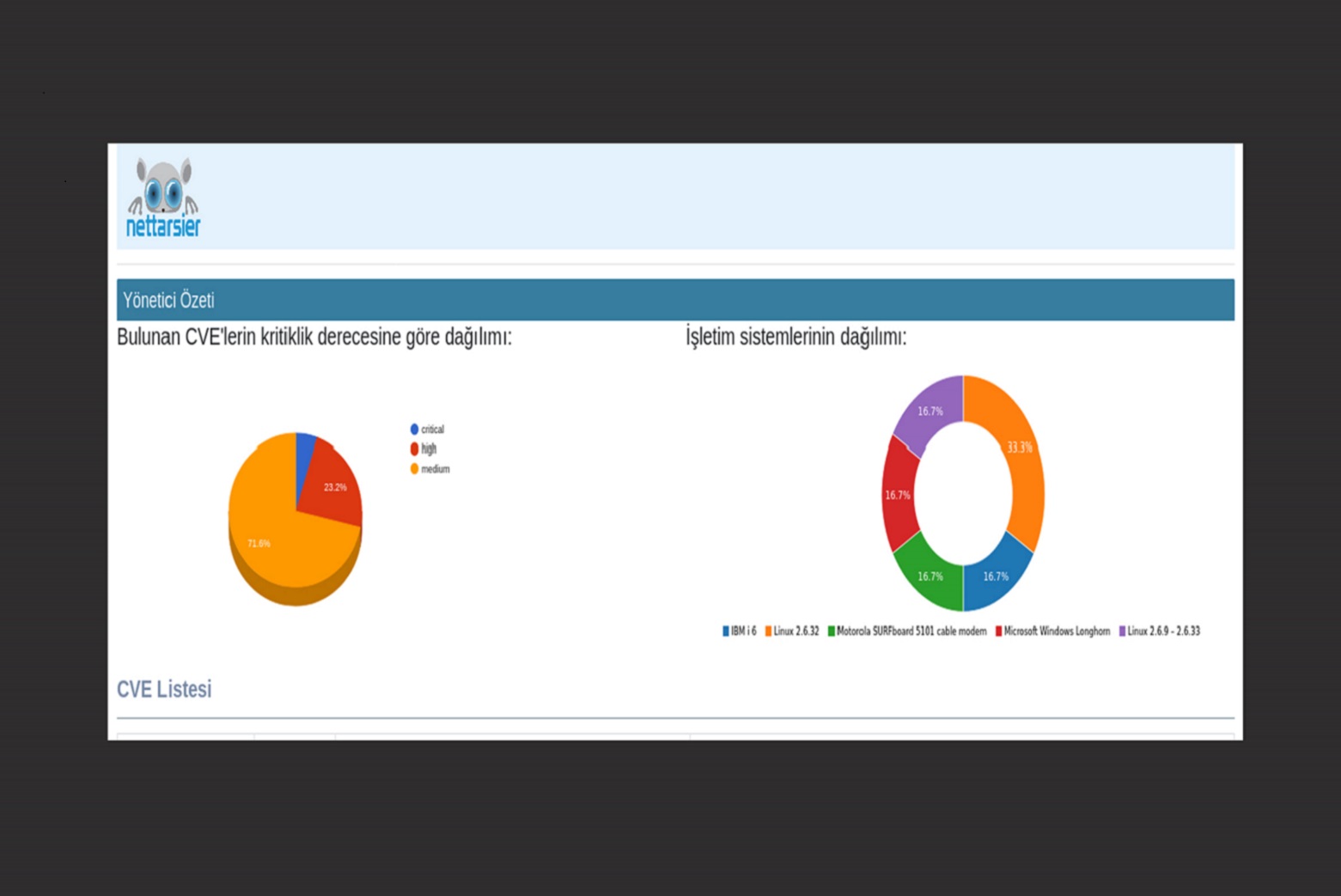
TIt provides an understandable simple Result Report with Executive Summary.
ADVANTAGES
You can take action on the top layer of your topology before threats reach your other security devices.
-
PROCESS FOLLOW-UP
TIt ensures that the detected vulnerabilities are assigned by the manager to the responsible person via the Task Assignment screen, the relevant person is informed by e-mail and the process is followed.
-
LOG FEED
It can provide log feed in json and syslog format via API library to SIEM and other security products operating in the Cyber Operation Center.
-

ACCESS PROTECTION
It allows the easy entry points of the systems to be closed by automatically testing the predictable default user names and passwords on the target services.
-
BLIND SPOT ACCESS
Its architecture reflects a methodological approach to penetration testing and ensures that there are no blind spots in the scanning process.
-

OFFLINE ACCESS
It can also work offline in the Intranet Corporate Network environment.